Uplink v3: Faster & Safer Automation Fabric 🅴

Scott Weinert
Co-Founder and CTO

Uplink is a critical technology in the Atomic stack, powering unique experiences such as TrueAuth - the first adaptive automation framework that keeps user credentials on their device. We’ve made improvements over the years, including the implementation of RPC (Remote Procedure Calls) which led to notable gains in connection reliability & speed. We’ve found that the deeper we go into the raw building blocks, the more opportunities we find to improve.
Here are some exciting developments we’d like to cover:
- We created a new protocol, so creatively named Uplink Message Protocol (UMP). It is safer, and according to our benchmarks, it is blazing fast.
- A newly issued patent number US 12,445,443, builds on our original patent, deepening our commitment to secure on-device automation technology.
- We’re opening it up for the world to build on, with early customers already in production.
Heads up: This is the explicit 🅴 version of the article, geared towards an audience that wants technical detail. If you're not into that, we recommend getting a "clean" version by plugging it into your favorite LLM, like this.
🧩 Overview of UMP
Why we built it. Automation acting inside authenticated sessions needs messages that are both fast and trustworthy on their own—not just secure pipes. JSON over WebSockets is ergonomic, but it adds parsing, copying, and framing overhead into the critical path and places trust in the connection rather than the message.
What it is. UMP is a compact, binary transport that lives beneath URPC (compressed JSON RPC) and above WebSockets. It adds per‑packet signatures, optional encryption, ordered delivery with acknowledgments, and multiplexed flows—all without giving up developer ergonomics at the RPC boundary.
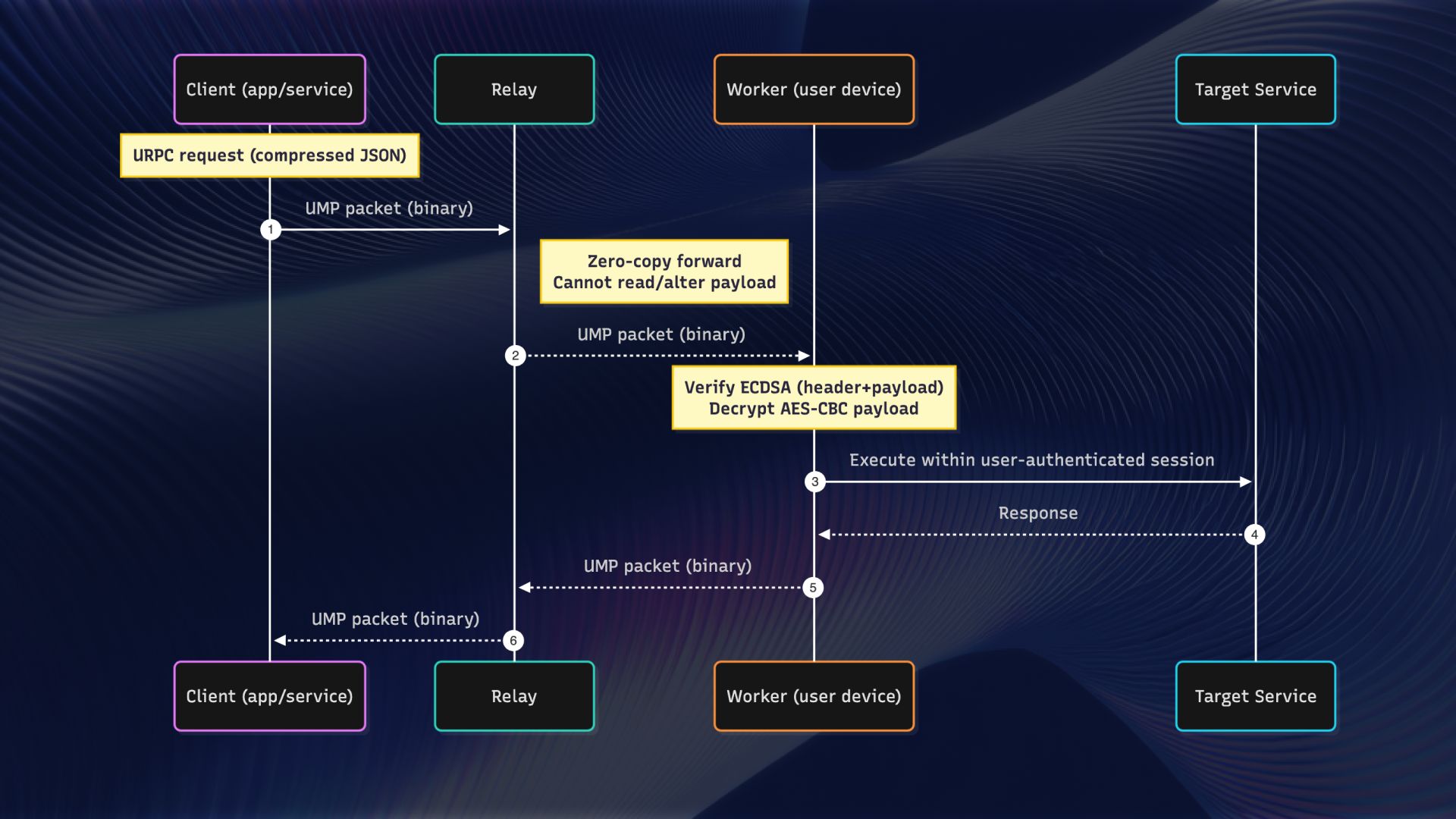
How it works. Traffic flows Client → Relay → Worker (user device) → Target Service. Relays route blindly; only the worker can decrypt and act. The target service sees normal, user‑session requests—no shared credentials and no proxy logins.
What changed under the hood.
- Per‑packet authenticity. Every UMP packet carries an ECDSA‑P256 signature over header and payload—tampering is rejected before processing.
- Confidential payloads. Optional AES‑256‑CBC with unique IVs per packet—relays forward at wire speed but can’t read contents.
- Streams, not bottlenecks. Multiple ordered flows on one connection with explicit sequence/ack semantics—no head‑of‑line coupling across tasks.
- Zero‑copy framing. Packets encode/decode directly from shared buffers—reduces allocations and parsing overhead that slow real‑time automation.
⚡ Performance
Bottom line: Zero‑copy UMP paths are 6–20× faster than copy‑based methods and up to 380× faster than JSON transport work. The larger the payload, the bigger the advantage.
Benchmarks — average latency. “Speedup” compares zero‑copy vs JSON.
| Group | zero | copy | json | Speedup |
|---|---|---|---|---|
| decode-encode | 69.6 ns | 424.5 ns | 606.6 ns | 8.7× |
| decode-encode-large | 69.2 ns | 503.1 ns | 13.1 µs | 189× |
| modify | 5.1 ns | 4.1 ns | — | — |
| modify-encode | 15.9 ns | 345.1 ns | 6.1 µs | 383× |
Why this happens: JSON’s costs balloon with payload size (stringification, parsing, copying), while UMP’s zero‑copy path stays close to constant. Big automations feel instant.
🔐 Security model
In Uplink v3, trust rides with the message, not the socket. Relays can route packets at wire speed but can’t read or modify them; only the worker on the user’s device can decrypt and act within the session.
- Ephemeral handshake: Peers exchange ECDH (P‑256) keys during the flow handshake to derive per‑session AES keys—no long‑term secrets on the wire.
- Per‑packet protection: Each packet is ECDSA‑P256 signed (header + payload). Payloads may be AES‑256‑CBC encrypted with a unique IV; headers stay routable but integrity‑checked.
- Replay & tamper‑resistance: Monotonic sequence/ack per flow; any header or payload change fails signature verification and is dropped.
- Relay transparency: Infrastructure forwards zero‑copy buffers without decryption or re‑signing; it can’t forge or alter packets.
- On‑device boundary: Signing keys live on the device; verification happens before any decrypt or processing.
🧭 Patent spotlight
US 12,445,443 — Securely Communicating Data Between an Application Associated with an Entity and a Third‑Party System. This grant extends our original patent to more broadly cover on‑device automation: embedded SDK in partner apps, detection of real authentication state from native login flows, and execution via secure RPC within the user’s authenticated session.
Together with our first patent, this formalizes the architecture behind on-device automation solidifies Atomic's long-term commitment to a best-in-class solution.
🌍 Opening it up
Demand for agentic automation now spans healthcare, logistics, commerce, and more. We've decoupled the rails we've used across millions of highly regulated and sensitive operations for everyone to build on.
- Early customers are already live on Uplink and operating at scale.
- Developer tooling is in progress to make integrations straightforward across industries.
- The goal: a secure, message‑driven layer anyone can add to their stack—where credentials stay local, sessions remain real, and automations fly.
Uplink started as a bridge, and is evolving to be the fabric that enables secure automation everywhere.


